“Cyber security is widely perceived as one of the most prominent threats facing society today,” begins our latest report Cyber Security in Smart Commercial Buildings 2017 to 2021. However, this is not necessarily because attackers are infiltrating society’s most important systems but because seemingly inconsequential elements can act as an entry point for a whole network of vital assets.
Attackers seeking entry into corporate networks will often seek out the path of least resistance. The interconnected nature of the Internet of Things in Buildings (BIoT) means that cyber attacks can pose risk far beyond the initial point of entry. Potentially causing cumulative damages that could potentially permeate into new layers of the enterprise, building and facility portfolio, users, operators, and service providers.
In November 2013, a breach of the point-of-sale (POS) system of US retail giant Target led to the acquisition of credit card and other personal information for nearly 110 million customers by the cyber attackers. The critical information was immediately distributed to an untraceable collection of international locations before the corporation had time to react.
The POS system, which holds masses of sensitive customer information, was not the initial focus of the attack however. Assailants had simply stolen network credentials from an external contractor working on the heating, ventilation and air conditioning (HVAC) system of one Target store. From there they were able to infiltrate the firms centralized Building Automation System (BAS) and find a way into the POS system that Target thought was secure.
“The impact of the breach was clearly exacerbated by the fact that the company had not properly segmented its data network, although systems alerts were generated during the breach as the attackers moved around the network, it has been reported that these were not acted on until after much of the damage was done,” explains our report, in one of many cyber security case studies.
When the dust settled, Target was forced to pay a total of $39m to banks who were obliged to return stolen money to their customers, but the cost of the breach was estimated to be much higher. By the end of 2014, the firm reported a gross financial loss of $252 million related to the breach and the continuing reputational impact to the brand is both incalculable and undoubtedly vast.
This example demonstrates some threat posed by highly networked enterprise BAS but the same could be true for a wide variety of public or private organizations. Individual building systems that control the HVAC, lighting, access control or other building functions, where they are connected directly to the Internet, may act as viable entry points to wider building or enterprise systems for a would be attacker.
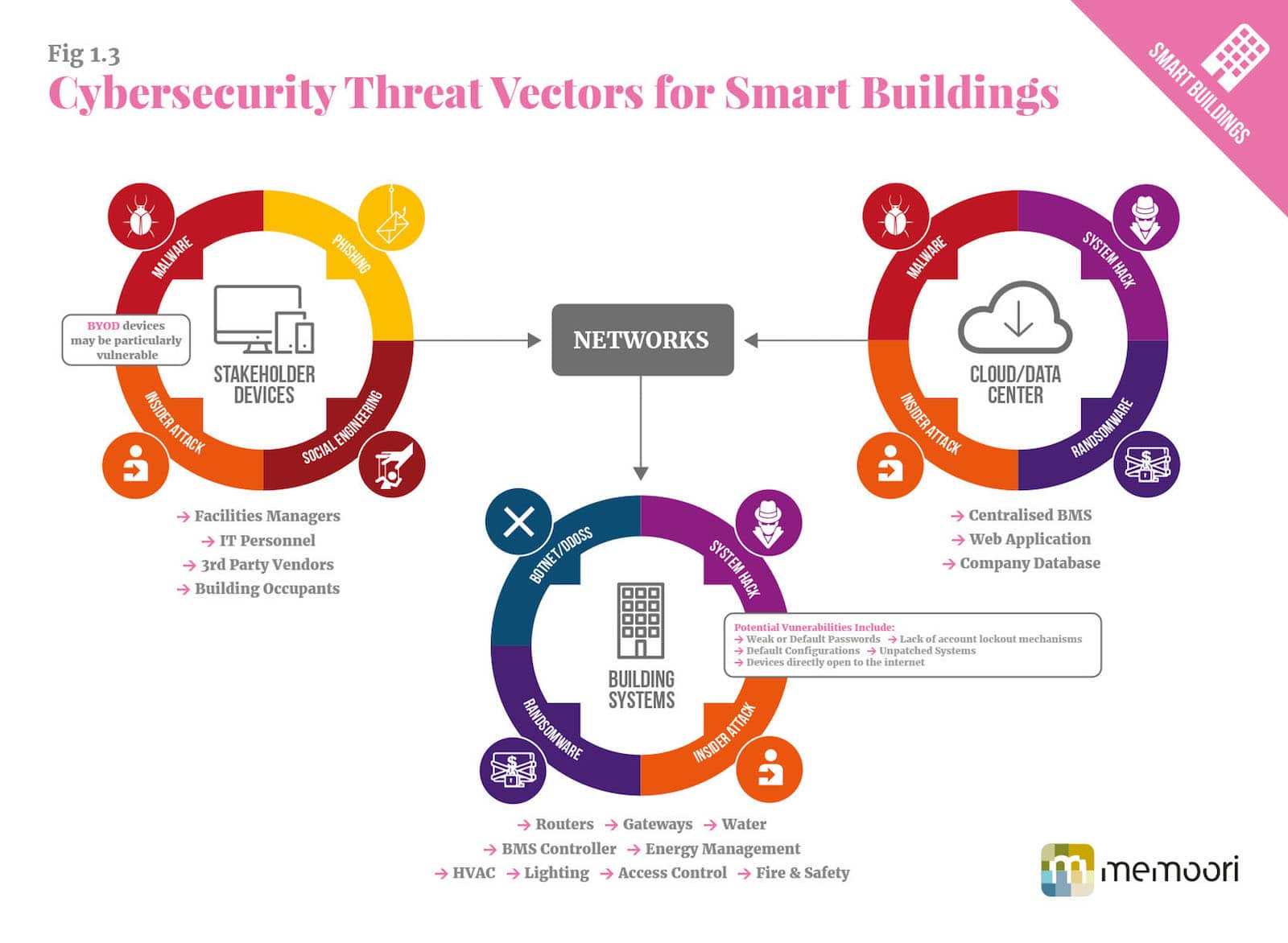
According to Fred Gordy, director of Cyber security at Intelligent Buildings LLC, as much as 80% of the time, an attacker’s aim is to infiltrate the network via a BAS, and to get past those controls to accomplish a larger goal or seek a more specific target. As we dive deeper into the internet of things (IoT) it is not just BAS that creates vulnerabilities.
Organizations that have adopted a centralized approach to building management, through a building management system (BMS) hosted in the cloud could provide the vector for an attack. Network routers, gateways, cloud and Web servers all have the potential to provide potential entry points to a network. The vast number of network connections and servers managed by data centers mean those facilities are highly targeted and any breach could be catastrophic.
Even so called “Bring Your Own Device” (BYOD) policies, increasingly seen in all manner of buildings, can create security vulnerabilities. Security protocols adopted by the average user, on their own personal devices, may not conform to the criteria required to protect a network, potentially making a single mobile phone the weak leak that brings down an organization.
It is clear that a more holistic approach to cyber security is required in smart commercial buildings. “In order to determine potential system vulnerabilities in a modern networked Smart Building, one must also carry out an assessment of the systems, devices and networks that are connected to building automation and control systems,” our report states.
This is not a one-off assessment but a strict and continuous monitoring of current and new network elements. Any building device connected to the IT network can act as a bridge to wider enterprise systems, which means the connected coffee machine might be just as important as the financial bookkeeping system to a cyber security professional.
“Where possible, systems should be isolated to limit the potential of a would be attacker to “pivot” or “bridge” between different systems on a network, through the adoption of stringent access control, authentication and permissions protocols on systems within a network,” our in-depth report advises.
If we are to enjoy the benefits our connected buildings will bring, we must also protect against the seemingly small elements that have the potential to bring our digital world crashing down around us. Even, as the case may well be, by restricting the beautiful freedom our smart world promises.
For more information, visit the report website and view our Cyber Security Infographic below. You can also download a PDF copy of our Infographic Here.

[contact-form-7 id="3204" title="memoori-newsletter"]